TidBITS#1254/12-Jan-2015
At the top of the news this week is the Thunderstrike proof-of-concept attack, which shows how Macs can be exploited at the hardware level. Security Editor Rich Mogull explains why it’s a serious threat, but probably not to you. AT&T is now offering rollover data, which is great, but Glenn Fleishman explains why some of the company’s other recent moves aren’t so positive. Workflow is a powerful new iOS automation app, and Managing Editor Josh Centers details what it can do. Contributor Mariva H. Aviram joins us this week for the first in her series on computing for the visually impaired. Mariva shares the challenges of her own temporary visual impairment, as well as those faced by people she knows. Finally, in FunBITS this week, Josh tackles Trivia Crack, explaining why the game is popular despite its many annoyances. Notable software releases this week include Little Snitch 3.5.1 and ChronoAgent 1.5.
Thunderstrike Proof-of-Concept Attack Serious, but Limited
[Update: Apple’s OS X Yosemite 10.10.2 Update (see “Apple Releases OS X 10.10.2, iOS 8.1.3, and Apple TV 7.0.3,” 27 January 2015) does prevent the current proof-of-concept Thunderstrike attack from being able to rewrite the boot ROM, but pre-Yosemite Macs remain vulnerable. -Adam]
Researcher and hobbyist Trammell Hudson has demonstrated an extremely serious, and fascinating, hardware attack against Macs. Dubbed Thunderstrike, the Thunderbolt-based attack is limited to situations where an attacker has physical access to a Mac and enough time to run it through a reboot and firmware installation cycle. Apple has partially addressed the vulnerability in recently released hardware (the iMac with Retina 5K display and the new Mac mini) and will be rolling out fixes to older hardware in the future.
Two aspects of the Thunderstrike proof-of-concept make it particularly serious. The first and most obvious is that most Macs remain vulnerable, and no antivirus software can help since Thunderstrike completely circumvents the operating system. Second, were Thunderstrike to be used to install malicious code, it would be hidden in a part of the system inaccessible to the user (the boot ROM, which is really a rewritable EEPROM chip) and would persist even if the boot drive were swapped out.
On the plus side, Thunderstrike is just a proof-of-concept right now — the demo shows only that an attack is possible, and doesn’t maliciously modify the boot ROM. Plus, it’s currently specific to particular Macs. But as Hudson notes, weaponization and targeting additional Mac models would be within the means of a dedicated attacker, which is why Apple is taking Thunderstrike seriously.
How Thunderstrike Works — The deep details of the Thunderstrike attack are extremely complex, so I’ll stick to covering it at a high level. Macs, like all computers, have firmware that swings into action when you push the power button, booting up the computer, loading the operating system, initializing hardware, and performing other functions. Some technologies, such as FireWire and Thunderbolt, interact with this firmware at an extremely low level, below Mac OS X itself, for feature and performance reasons.
The Thunderstrike proof-of-concept takes advantage of this trust to replace the contents of the Mac’s boot ROM with the attacker’s own code, effectively embedding it into the Mac’s hardware and making it impossible to remove using standard techniques. The attack works because Apple relies on software checks to confirm the firmware is valid, and Hudson developed techniques to circumvent those checks (and even replace the encryption key).
To take over a Mac, the attacker needs physical access. He then plugs in Thunderstrike-enabled hardware — a modified Thunderbolt-to-Ethernet dongle in the demo — and reboots the Mac, triggering the process that replaces the firmware with malicious code. That’s it.
Hardware attacks like this aren’t new. There are actually a number of ways to leverage physical hardware access to compromise a computer. For example, FireWire supports something called Direct Memory Access (DMA) which has, at times, allowed attackers to plug into the FireWire port and directly read and manipulate memory (this fact was used in the famous FireStarter hack at MacHack a dozen years ago — see “The MacHax Best Hack Contest 2002,” 1 July 2002). I even once designed an attack against my Commodore 128 by reprogramming the firmware on my external floppy disk drive; luckily, it seems my 14-year-old self lacked the technical skills to make it work, leaving the world safe.
Most of these sorts of hardware attacks are limited in the sense that they modify memory or the operating system, not the boot firmware, which is one of the most difficult parts of a computer to fix. Firmware malware may not be common, but it’s such a concern that some of my enterprise clients bring only disposable hardware when traveling to certain countries.
Thunderstrike is particularly interesting because of Hudson’s innovative techniques and because the basics of the attack may lend themselves to combinations with other techniques that could circumvent Apple’s current round of fixes.
Who Thunderstrike Could Affect — While all Macs are technically vulnerable to the Thunderstrike attack, few TidBITS readers face any immediate risk. The attack is highly targeted — someone needs both physical access to your Mac and time to reboot it and reinstall the firmware. On top of that, it isn’t like everyone is walking around with maliciously modified Thunderbolt dongles. This focuses the risk on three situations:
- International business travelers who may be attacked when giving up physical control of their Macs at customs, or when leaving their computers in hotel rooms in potentially hostile areas. My security work means I fall into this group, so I have taken some extreme precautions over the years to prevent this sort of physical attack.
- Unattended Macs at kiosks or in computer labs.
-
Anyone in a hostile living situation.
There’s also always the chance an attack could be aimed at retail hardware somewhere in the supply chain, as we’ve seen with malware on digital photo frames, but this is likely a low risk since Apple is already closing the vulnerability.
Aside from updating your Mac when firmware updates appear, your best defense is to maintain physical control of your computer at all times. This might sound extreme, but there are places I travel where I won’t even bring my Mac for fear of it being compromised while crossing the border. Again, almost no one reading this article is at risk.
Firmware attacks have existed for many years, and if recent security conference agendas are any indication, we’re likely to see more of them in the future. Fortunately, they are self-limiting due to the need for physical access, but for those at risk, they remain extremely concerning.
AT&T Offers Rollover Data While Defending Throttling
AT&T has a lot of strange ideas about mobile data. The company is trying to fend off competition, while simultaneously squeezing grandfathered unlimited data users and extracting profit from new corners of the industry in ways that may violate notions of network neutrality.
Mobile Share Value Adds Rollover Data — Let’s start with the good. About 50 million AT&T mobile customers who have its Mobile Share Value plan will automatically have unused data from one month added to the available pool for the next month. This Rollover Data feature doesn’t require activation. Data will start rolling over on account cycles starting 25 January 2015. About 70 million customers don’t qualify, including legacy Mobile Share customers and prepaid subscribers.
AT&T charges overages on its Mobile Share Value plans at rates of $20 per 300 MB for its 300 MB plan, $20 per 500 MB for its 1 GB plan, and $15 per 1 GB on its 3 GB and higher plans. Plans are available from 300 MB to 100 GB, and costs are based on data plus devices. A 1 GB plan costs $25 per month plus $25 per unsubsidized smartphone or $40 per phone under a two-year contract (including unlimited voice time and texts). A 10 GB plan with two phones would run $100 plus $15 per phone, for a total of $130 per month before tax.
Unused data rolled over from a previous month expires at the end of the current month, unlike the way that rollover calling minutes used to work (and sometimes still do) with limited calling plans, where rollover minutes persisted for a year. For those who go over their limit occasionally, Rollover Data could save non-trivial amounts of money.
Imagine you have a 10 GB plan and use 5 GB in November, 12 GB in December, and 3 GB in January. Your unused 5 GB from November would roll over to December, removing the $30 overage fee, but no data would roll over from December to January. The 7 GB unused from January would roll over to February, however, making 17 GB available without risk of overage fees.
You can see how paying occasional overage fees could dramatically increase overall cost, encouraging users on older plans to migrate to a Mobile Share Value plan with Rollover Data, despite the limitation of a single month’s data rolling over.
A similar T-Mobile upgrade announced in December 2014 rolls unused data over for up to a year. T-Mobile doesn’t charge overage fees; rather, after your contracted allotment is up, it throttles your data rate to 64 Kbps or 128 Kbps for the remainder of the month. More on throttling below.
My family upgraded as we had no legacy grandfathered data offerings, and AT&T’s Mobile Share Value plan increased our data cap from 3 GB to 10 GB for $10 less per month. Since we rarely approach the limit of our plan, we might consider dropping our data cap to 6 GB, which, due to the vagaries of per-phone pricing, would reduce our monthly cost by $15 per month.
Hard Throttle Back, Carriers — On a less pleasant front, AT&T is defending its throttling of grandfathered unlimited data plans and expanding its program to allow companies to pay AT&T directly to avoid tapping into your monthly data pool. T-Mobile was recently dinged by the FCC for not disclosing its throttling rates and terms as well.
For those who may not recall, when Apple introduced the iPhone in 2007, the initial data plans on AT&T (and later on Verizon Wireless) were unlimited, which became problematic for the carriers when iPhone sales went through the roof and their network expansions didn’t proceed as quickly as anticipated.
In 2010, AT&T killed unlimited data plans for new customers, and other carriers soon followed. (AT&T has a hilarious “pity us” site about this.) However, those who kept their original plans and transitioned phones were allowed under contract to keep unlimited data. The carriers have tried various incentives to get people to give up on these plans and shift to tiered plans with limits and overage fees.
In 2012, AT&T decided that it should put the screws on unlimited-plan users, and began throttling what it called its “top 5 percent of users,” which could mean people who exceeded just a couple of gigabytes a month. More recently, AT&T established a policy of throttling data speeds after 3 GB of data usage on 3G or “4G” (really 3G+) networks and after 5 GB of data usage on 4G LTE phones, regardless of what network style is in use.
In October 2014, the FTC called foul on this, suing AT&T and noting that throttling is “deceptive” and “unfair,” two tests the FTC uses to bring cases. This is similar to a 2007 case in which Verizon settled with New York State after an investigation into the company throttling a mobile data plan advertised as “unlimited.” Verizon also pulled back on plans to throttle 4G LTE customers.
Note that lawsuit came from the Federal Trade Commission, which handles consumer issues, not the Federal Communications Commission, which deals with regulation and compliance for telecommunications and related industries. The FTC said it worked closely with the FCC. In a filing to have the FTC suit dismissed, AT&T said on 8 January 2015 that the FCC is separately considering fining it over the same issue, and that the FTC lacks the authority to proceed.
T-Mobile got into hot water over throttling last year as well. It said in August 2014 that it wouldn’t throttle its unlimited data customers, despite a leaked memo that said it was going to squeeze customers who violated terms and services — including “heavy” data users, a term that remained undefined. T-Mobile has the option to throttle all of its customers already, and was forced by the FTC in November 2014 to clarify those
limits — subscribers are knocked down to 64 Kbps or 128 Kbps speeds, depending on their plan. However, it hasn’t yet had to backtrack on its unlimited plan.
Meanwhile, AT&T has begun selling “subsidized” services to a few businesses, now numbering 10. These companies can provide data to AT&T customers that doesn’t count against monthly data usage totals. The companies in question are quite small, and don’t include any major consumer, business, or media brands. The program could be construed as violating net neutrality in a loose sense, by providing a channel for some companies that isn’t available to others except for a fee, rather than, say, a higher-speed path for those who pay.
Monitoring the Situation — The trouble with how AT&T and other carriers approach this situation is that they are trying to mitigate what might be very reasonable problems by changing terms of service and redefining English words. These legal tactics damage their reputation, and encourage consumers to switch services.
You might recall that AT&T wanted to buy T-Mobile in 2011, and fierce opposition from the FCC and the Department of Justice quashed the deal. The government’s argument was that such a merger would reduce America to two major networks (AT&T/T-Mobile and Verizon) and one medium-sized one (Sprint). T-Mobile’s behavior following the deal’s cancellation proved the point: we would all be paying more for less if T-Mobile had been acquired.
The Rollover Data plan from AT&T is more of what we should see: carrots, not sticks based on throttling. If AT&T wants its grandfathered unlimited users to give up the plan, the company should offer them something comparable and eat the cost up front. Give them all 100 GB-per-month plans and a free iPhone — something that compensates for the loss, provides AT&T with more predictable network usage, and eliminates this relentless stream of petty and negative behavior.
Workflow Is the Next Step for iOS Automation
Since Mac OS X 10.4 Tiger was released in 2005, Mac users have had access to simple, built-in automation with Automator. Third-party developers have spent years trying to replicate Automator’s power and simplicity on iOS.
If you use iOS more for consumption than creation, you might wonder why you’d want to automate iOS at all. Easy as iOS is, if you think about it, there are probably common tasks you can make easier by stringing multiple actions together. For instance, wouldn’t it be nice to call your spouse with one tap on a Dock icon? Or shorten a URL with a custom service and post it to Twitter? Maybe you take a lot of baby pictures, and would like to send the most recent photo to the grandparents quickly? Or if you’ve had a bit much to drink at a party, wouldn’t it be nice to request a car from a service like Uber to take you home with only a tap or two? These are all possible to automate on iOS. Just as with Mac automation, you can probably
come up with a lot of ideas for common tasks to automate with just a little thought.
The most notable third-party development in iOS automation was x-callback-url, a clever, if kludgy, standard developed by Greg Pierce of Agile Tortoise. Before the days of Extensibility in iOS 8, x-callback-url was the main way apps could toss information back and forth across iOS’s sandbox wall to communicate with each other.
This led to some interesting experiments with iOS automation. Agile Tortoise’s own Drafts app lets you jot down notes and share them with other apps and services, among other things. Launch Center Pro enables you to launch multiple apps from one place, as well as automatically perform certain actions with some of those apps. Then there’s Editorial, a powerful text editor that can be customized with the Python programming language and that can use x-callback-url to process text from other
apps.
While these are all fun to play with, and are useful for certain people (like Federico Viticci of MacStories, who has written extensively about his experiments in iOS automation), they’re too difficult for average users. You either have to learn a foreign syntax or work around the many limitations of iOS to get anything done.
Those concerns might now be moot, thanks to DeskConnect’s Workflow ($2.99 in the App Store), which is the closest iOS has come to Automator’s powerful simplicity.
What sets Workflow apart from past iOS automation efforts is that you can create workflows visually, with no traditional programming required. The design of the app is bright and friendly, making it ideal to learn or teach the basics of programming.
The beauty of Workflow is that you don’t have to be a programmer to take advantage of it. The app comes with useful, built-in workflows, and it offers a gallery of other workflows you can download. Users can also share workflows over the Web.
So what can you do with these workflows? Here are a few examples:
- Send someone your estimated time of arrival
- Call an Uber car to take you home
- Get the lyrics of the currently playing song
- Upload the last photo taken to Dropbox
- Shorten a URL
- Make an animated GIF from a series of photos
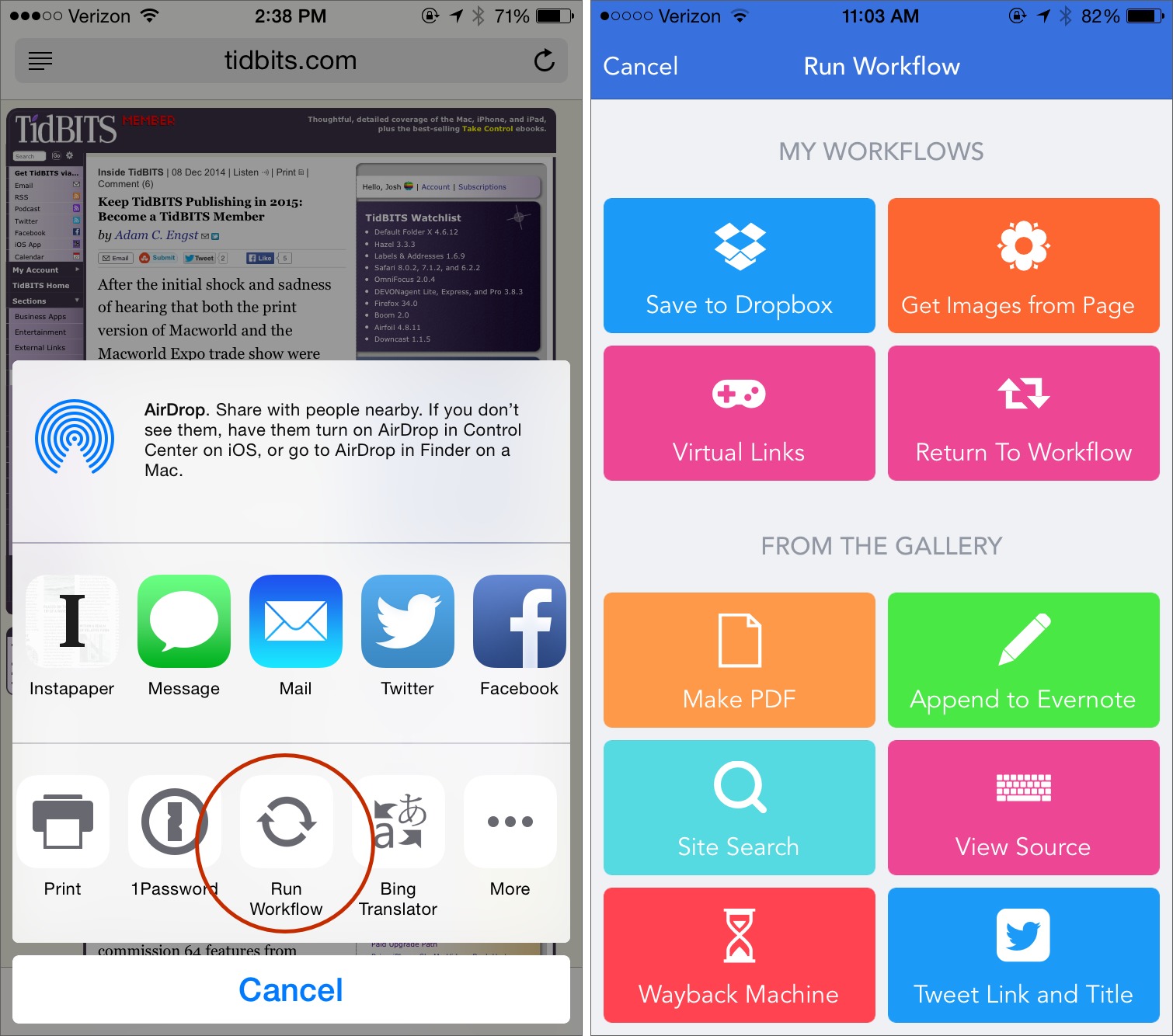
You can put workflows on your home screen as icons, or use them within Safari as action extensions. To use Workflow inside Safari:
- Tap the Share button in the toolbar.
- Scroll the bottom action row to the right and tap More.
- Toggle the Run Workflow switch.
To call a workflow from Safari, tap Share, and then Run Workflow. You’re presented with workflows that you have designated as action extensions, as well as potentially useful extensions from the app’s gallery.
To my mind, Workflow is worth the cost of admission just for the way anyone can use it to extend Safari’s capabilities. With a few downloads from the gallery, you can save a full Web page to Dropbox, export a Web page as a PDF, extract all images from a Web page, view a Web page’s source code, search the Web site, or even view an older version of the page on the Wayback Machine. Federico Viticci has made a custom
workflow to append the title and URL of the current Web page to an Evernote note, which I find handy when compiling ExtraBITS candidates.
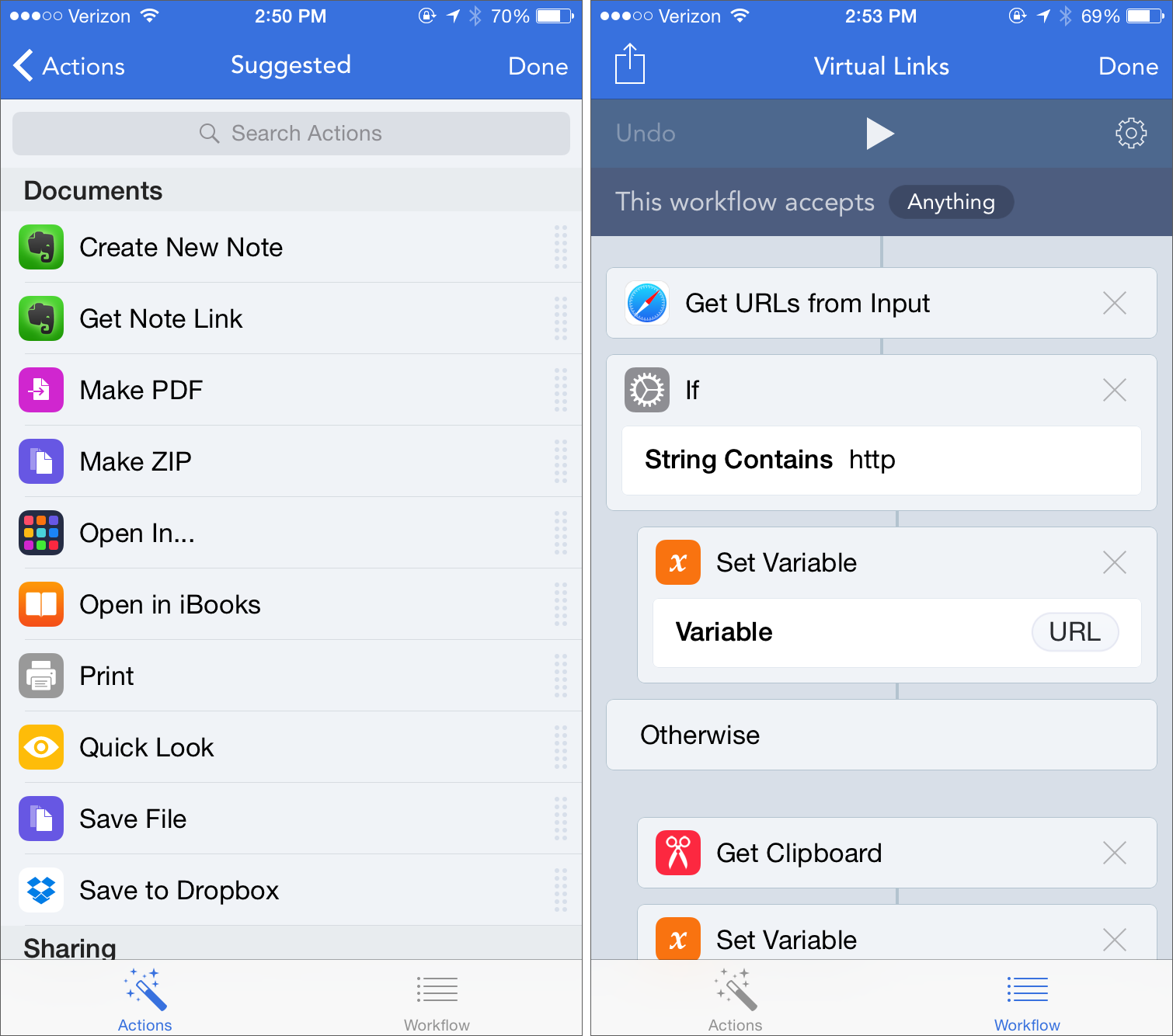
The way you create workflows is interesting. You start in the Workflow view, which comes with a few pre-installed examples. From the My Workflows view, tap Create Workflow. To add actions to a workflow, switch to the Actions pane, which lists actions in different categories. If you know what you want, you can search for a particular action. Once you see an interesting action, tap it to see a description, or drag it into your workflow. You can tap the Play button to run a workflow at any time for testing. From the Workflow view, you can also set a workflow as Normal or as an Action Extension — the former works as a standalone workflow, while you invoke the latter from the Share menu in other apps.
Workflow programming is entirely linear, with each action executed in order, from top to bottom, much like Automator. Actions that take inputs get them from the preceding action. Also like Automator, you can use the Set Variable action to store the output of a preceding action, then use the Get Variable action to recall that output. It’s a bit different from what most programmers are accustomed to, but anyone familiar with Automator shouldn’t have trouble grasping the concept.
Unsurprisingly for an initial release, Workflow has some rough edges. Its gallery can only be browsed, and is in desperate need of a search feature. The best way I’ve found to search for new workflows is a workflow that searches Tweetbot for other workflows, but that’s far from ideal.
Another annoyance is that you have to watch Workflow working through each workflow’s steps every time you activate it, even if you launch it from the Home screen. It would be nice if a workflow could hide its underlying actions like any other app, but I imagine that’s an iOS limitation. To see what it looks like to work through a complex workflow, here’s a video that demonstrates using Workflow to create a TidBITS Amazon affiliate link.
While I’ve only just begun to play with creating workflows like the one above, I’ve already encountered one frustrating limitation. Like most programming interfaces, Workflow features an IF statement to test if a condition is true or not and act accordingly. Unfortunately, it can evaluate only strings of characters, and not whether a preceding action succeeded. I’d like to create a workflow that would check to see if an Evernote document exists, and either append a note to it if available, or create one if the document doesn’t exist. Unfortunately, that isn’t currently possible.
But as I said, you don’t have to be a programmer to get use out of Workflow. Its gallery already features a number of useful workflows, with more sure to come. For $2.99, it’s a handy tool to keep on your iOS device. While automation isn’t for everyone, I encourage you think about repetitive tasks you perform frequently on your devices and give Workflow a try. You might be able to save more time than you would initially expect!
Computing for the Visually Impaired, Part 1
If you have fully functioning eyes, conduct a thought experiment on how you would navigate your life without them. How would you earn a living, keep up your home, maintain personal hygiene, take care of your loved ones, and transport yourself from one place to another?
Now reduce the experiment to just one significant area of your life: digital data. How would you communicate with people, access your personal information, pay your bills, track your finances, and submit your work? Even for those of us whose jobs don’t involve computers — which is increasingly rare — much of our lives involves electronic screens and digital data. For “knowledge workers,” computers are integrated into the things most important to them: work, identity, creativity, and connection.
Viral Conjunctivitis and My Terrible, Horrible, No Good, Very Bad Weeks — In the spring of 2014, my left eye began exhibiting the symptoms of a particularly severe case of viral conjunctivitis. Within the space of 36 hours, the area around my eye swelled to the size of a golf ball. After at least 12 hours, when I was finally able to crack open my eyelids, the garish rainbow colors of my lumpy, swollen conjunctiva (the clear membrane above the sclera — the white part of the eyes) shocked me and both the acute pain and my unremittingly blurred vision frightened me.
(For more details of the Lovecraftian horror of this particular experience, search for “epiphora,” which was voluminous, and for “purulent exudate” (you do not want to browse through Google Images results for those searches). Thankfully, I was fortunate enough not to have grown new membranes over my conjunctiva, which is apparently symptomatic of even worse cases than mine.)
During the first few days of physical and emotional trauma, I was consumed by anxiety over my growing pile of undone tasks and chores, and then by the sheer boredom of attempting to occupy my mind while my eyes remained closed. Even setting up a series of podcasts to listen to would have overtaxed my good eye. After a week or so, I faced the daunting challenge of figuring out how to use a computer — or any screen. I had never fully appreciated how crucial, yet fragile, eyes are.
To deal with my sundry visual frustrations, I made as many adjustments as possible. For example, I stopped wearing my prescription eyeglasses. I found my uncorrected vision to be workable when using an iPad, but much less so with the MacBook Pro. My good eye had to compensate for my infirm eye, and so the good eye ended up doing most of the work of both. However, keeping my bad eye closed while my good eye darted around the screen rapidly led to eyestrain.
The iPad screen seemed too bright even at its dimmest setting and, unlike with a traditional computer, there aren’t numerous screen adjustment utilities. (After the fact, I found Dimmer, which received mixed reviews, as well as several third-party Web browsers with screen-dimming features.) Due to extreme photophobia, I wore dark sunglasses while viewing the computer screen, even while it was fully dimmed. To make matters worse, the polarized lenses created additional visual interference.
Statistics on Visual Impairments — One question arose in my mind: How do people do this? Surely I can’t be the only visually impaired computer user who needs to get things done.
According to a 2012 CDC survey, outlined by the American Foundation for the Blind, 20.6 million American adults reported experiencing vision loss — which is close to 9 percent of all adults in the United States; those with actual visual disabilities comprise about 6 million adults. This increases exponentially as people age. Worldwide, 285 million people are estimated to be visually impaired. Since the use of digital screens is such an integral part
of modern life, these statistics are significant for tech developers and other intensive computer users.
It’s important to realize that visual impairments, and sensory deficiencies in general, can differ greatly from one person to another — and even from one eye to the other within the same person. From a product development perspective, it’s difficult to design adequate interfaces to accommodate different needs, especially since each user requires unique solutions and adaptations.
My own impairment, which left me with only one good eye — which was also hampered by photophobia and eyestrain — presented one set of challenges. Here are three other cases to consider.
Optic Nerve Damage from Meningitis — My brother, a senior software engineer, suffered damage to the optic nerves in both of his eyes from a bout of meningitis twenty years ago. As a result, he has blind areas that are different in each eye. These blind areas are not totally impervious to visual input, but his visual acuity in those areas is inadequate to read or recognize sharp outlines — except in one small center of vision in one eye, which he relies on to read, find a mouse pointer, and perform other tasks involving fine visual details. Upon recommendation by the Vision
Rehabilitation Center at the Massachusetts Eye and Ear Infirmary, he sets backlit screens to a very high level of brightness to ease reading and discerning fine detail.
In order to fit a readable amount of text into the one precious area of clarity within my brother’s eye, the type must appear as small and sharp as possible. (To this end, a “reducing glass” — as opposed to the commonly used magnifying glass — would be ideal.) For larger images, he relies on peripheral vision. This inconsistency makes annotated images such as diagrams particularly troublesome.
With these competing limitations, he encounters numerous frustrations with computer screens. If, due to time constraints (such as while giving a presentation), he cannot increase the pointer size, he simply mouses to the upper left corner in order to find the pointer, repeating this every time he “loses” the pointer. Moving his eyes away from an area of focus and back is especially disruptive because of the difficulty in finding his original place. Another big time-waster is searching through a Web form to find a field or the submit button. Keyboard shortcuts often circumvent these problems and, as an added benefit, streamline procedures.
Some arcane problems present themselves only during unusual circumstances. For example, the mouse trails feature in Windows can be useful, but only when working in Windows natively. When running Windows in VMware Fusion, the refresh rate is too slow, which renders the mouse trails in disorienting and distracting ways, with the mouse cursor seeming to flash within an area without its usually beneficial precise pointing.
Finally, solving one problem — such as inverting colors to ease the reading of text — sometimes creates another, such as also inverting colored images, which makes people appear as “ghouls and ghosts,” gives desktop wallpapers unpleasant hues, and makes many diagrams unreadable. Or, the mouse pointer, when increased in size, covers text and icons just when they need to be most visible. You can imagine the frustration.
Dry Macular Degeneration Causing Excessive Sensitivity — In contrast to my brother, who requires bright displays to see his work, I have a friend who is very sensitive to the brightness and contrast of LCD screens due to suffering from the early stages of dry macular degeneration. When he views a monitor straight on, he describes looking up at it “through his eyebrows” — meaning that he uses his eyelids to cover the pupil partially in order to create a pinhole-view effect. He blocks out much of the screen, focuses on just a line or two of text, and then looks down again.
His solution to the excessive brightness is to dim his screens with the free utility Shades, which competently manages multiple monitors. He also views monitors from above, which throws less light into his eyes. Nevertheless, he still experiences some artifacting, which can be distracting, particularly with a Twitter or mail client that has subtle background colors to indicate message status, Web page text with blue links that seem to cast a yellow haze around everything else on the page, and light text on a dark background that produces ghosted images of lines.
With regard to vision, my friend talks about making hard choices: not just with what he’s going to do, but with what he pays attention to — and even when he opens his eyes and for how long. “You have to choose what you’re going to look at,” he says.
Living in a Colorless World — Another acquaintance, a former software engineer whom I’ll call “Roy” (with a background in, of all things, information visualization and graphical display of complex data), is severely colorblind due to a rare eye disease called incomplete achromatopsia, or dyschromatopsia. In dim-to-medium indoor lighting, he sees only in grayscale. With increasing illumination, he can discern colors from the red to the blue end of the color spectrum. But as illumination increases, details become harder to see. He can’t discern washed-out or pastel colors under any conditions, and he
claims that he “fails every standard test of color vision miserably.”
Roy has poor visual acuity — he is legally blind in typical illumination conditions — even with his prescription eyeglasses. In addition, he suffers extreme sensitivity to light, which renders him nearly blind in sunlight if he’s not wearing specialty dark glasses with side shields. He also wears a hat or visor to block stray light from above. All of these symptoms and experiences are typical of incomplete achromatopsia.
(AchromaCorp is currently the only organization that specifically raises funds to develop treatments and cures for achromatopsia. For the cautiously optimistic, medical research group AGTC may begin conducting human trials within two years for a workable gene therapy to treat achromatopsia and other eye diseases.)
With regard to computer use, like many low vision users, Roy makes do with what he has. His primary operating system is Windows XP. He sets the style to Windows Classic, because the blue-and-green Luna visual style is “too visually cluttered and confusing.”
The bane of many a Windows user’s experience is Microsoft Outlook, and that’s no different for Roy, especially after Microsoft changed one of its key design features of Outlook. In previous versions, unread email appeared bolded. The color scheme now distinguishes read from unread mail with what appears to him to be “slightly different shades of gray, and in the same font, size, and boldness,” making it far more difficult for him to differentiate between types of messages.
Similarly, with the Outlook calendar, the color that distinguishes the Today box is almost the same brightness as the color of the appointment rectangles, which makes them difficult to distinguish for those suffering from color blindness.
Roy observes an increasing use of color coding to convey information that had formerly been conveyed via simple text or other graphical conventions. His coping strategy is to spend more time trying to discern what are to him the subtle differences in visual cues.
One positive recent trend in graphic design, however, is the “flattening” of icons, buttons, and other elements — a look-and-feel change that’s pronounced in iOS 8 and OS X 10.10 Yosemite — because it allows more of the screen real estate to be used for clearer images and larger text rather than for nonfunctional elements, such as 3D border shading or color gradations.
When viewing Web sites Roy simply enlarges the browser text as needed. Some Web sites, however, choose color schemes that render sites inaccessible for colorblind users. (Terrible palettes include blue text on a green background, yellow text on a blue background, red text on a black background, and any text on a busily patterned background.) If Roy needs to read such a Web site, he must highlight the text to do so.
Because of his light sensitivity, Roy reduces the backlight brightness to the lowest setting, but sets the contrast high. This is a paradox, though, because higher contrast also increases brightness, so it’s a compromise. He also sets the screen to a low resolution of 1024 by 768, which enlarges text to make it readable for him.
Roy doesn’t have a particular font preference, but text size is important. For composition, he sets the font size to around 20-point type (Arial), which is on the low end of ease of use for him. For reading long documents, such as ebooks, he sets the font size to approximately 36-point type or more.
When I first discussed this topic with him, Roy summed up the problematic recent design trends thus: “Computing is getting harder for people like me because users are expected to do ever more with ever smaller screens.”
Avoiding small screens altogether is becoming less of an option. These devices — which rely on minuscule font sizes; small, highly detailed icons, color coding; and visual clutter — are increasingly displacing traditional, more accessible media (print maps, business cards, landline phones), leaving those with poor visual acuity at a disadvantage. Even apps that enable zooming and scrolling are clumsy and time-consuming.
“These products aren’t designed by or for elders or for those with any kind of visual impairment, such as color defects or ambient light interference,” he laments. As a result, he doesn’t own a mobile phone.
Also, disabled people suffer much higher rates of crime victimization than the able-bodied (and the able-visioned). Roy feels particularly vulnerable to street crime because of his low vision and the dark glasses that block his peripheral vision. The proliferation of expensive mobile devices has exacerbated theft and related crimes in high-density areas, disproportionately harming people with low vision and other disabilities.
Preparing for Visual Impairment — I figured that there must be some help for people like me, and there is, to some extent. In hindsight, of course, the best time to have learned about such options was before I found myself disabled.
Preparing for the loss of vision is like disaster preparedness; most people don’t want to think about it. You hope that you’re never in such a situation, but if you are, you’re glad that you did at least some preliminary work to prepare. Familiarity with Accessibility preferences and third-party utilities is akin to installing quality, regularly inspected smoke detectors and fire extinguishers around your home.
While coping with my own affliction, I was inspired to learn more about other people’s experiences with visual impairment as well as about remedies and assistive technologies for people like us. In the next installment of this series, I’ll explore a variety of eye problems and share the advice of vision care experts.
Articles in this series:
FunBITS: Trivia Crack Simultaneously Attracts and Repels
Over the holidays, I found my house full of people sitting around, staring at their phones, and blurting out random questions. The cause? A new iPhone game called Trivia Crack, which has climbed to the top of the App Store charts. And, though my guests were all playing simultaneously (and asking for help from those present), the actual games were against remote friends.
Trivia Crack comes in both an ad-supported free version and a $2.99 paid version. If you like the free version, the paid version is well worth it to get rid of the many annoying video ads.
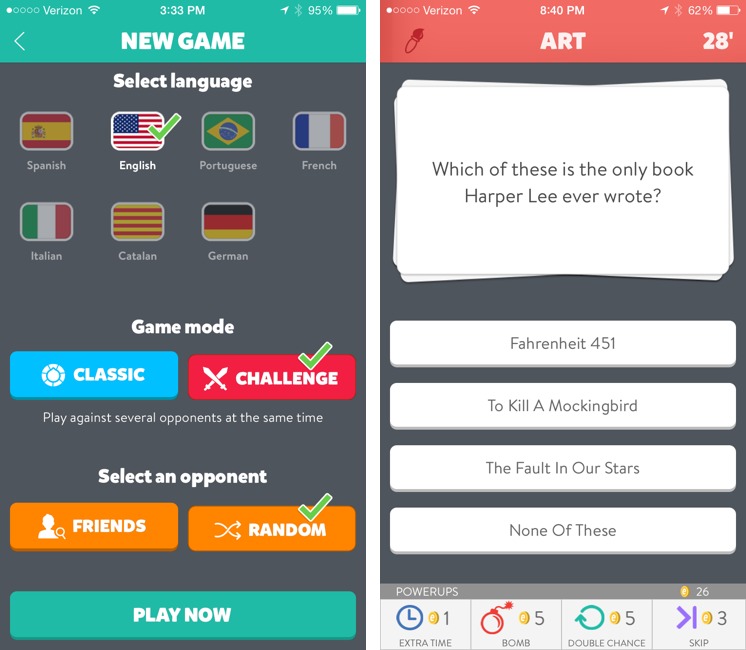
Trivia Crack is a take on the classic board game Trivial Pursuit. Answering trivia questions is the heart of the game, but there are two distinct gameplay modes: Challenge and Classic. In Challenge mode, you compete against up to ten other players, answering a barrage of questions, and whoever answers the most questions correctly wins.
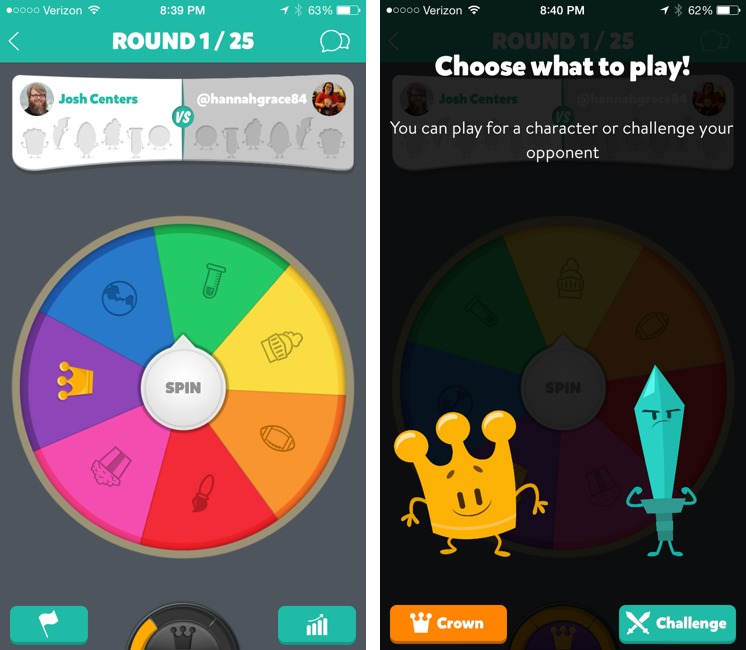
Head-to-head Classic mode is a little less straightforward. As in Trivial Pursuit, you win by collecting a set of colored pieces, called characters, with each color representing a topic: orange for sports, yellow for history, green for science, blue for geography, red for art, and purple for entertainment. The first player to collect all six characters wins.
You begin your turn by spinning the wheel, which randomly selects a category or the crown. If you get a category, you’re asked a question in that category. After three questions — or if the wheel lands on the crown — you can play to win a character of your choice or to challenge your opponent. If you choose to try to win a character, you get to pick the category from those remaining. You can also challenge your opponent to try to steal one of her characters, but that requires wagering one of your characters. Then you both answer a series of questions, and whoever provides the most correct answers wins both characters.
Of course, Trivia Crack wouldn’t be a contemporary iPhone game without purchasable helper items. You’re given three extra spins for free, which let you spin again if you don’t like a given category. More spins can be obtained via in-app purchases, as can coins, which are the game’s primary currency to obtain power-ups. Coins, which you also obtain upon completing a game, can be used to buy bombs to eliminate two wrong answers, extra time to answer questions, double chances to give you a second chance to get the right
answer, and the option to skip to another question.
How much you can play is limited by how many lives you have. You lose a life every time you start a game, and it takes a full hour to regenerate each life, up to a maximum of three lives. Even more annoying than in-app purchases, you can obtain additional lives by begging your Facebook friends to click to give you more. Please don’t do this. Thankfully, it’s not a huge restriction, because a game can take hours or even days to play, and lives don’t affect existing games.
Interestingly, Trivia Crack’s questions are created and vetted by the players. From the Question Factory, you can suggest your own questions, rate suggested questions, and translate questions into other languages. As you might expect, player-generated questions lead to some wonky or poorly worded questions. For example, one question asked who is most identified with physics, giving both Isaac Newton and Albert Einstein as choices. I correctly guessed Newton, but I fail to see how Einstein would have been incorrect.
It’s a brilliant, if cynical, business model for Argentinian developer Etermax. Users either spend $2.99 on the app or get hit with numerous video ads, users create and approve the game’s content, and some users pay extra to gain advantages over other players.
I’m somewhat uncomfortable recommending Trivia Crack due to its many questionable practices. Trivia Crack features just about everything I detest in an iPhone game: “pay to win” mechanics, social media begging, and occasionally sloppy user-generated content. What Trivia Crack has in its favor is the network effect: almost all of my friends are playing it, and its gameplay is compelling. Despite its annoyances, it’s a fun way to kill some time with friends, and if you can put up with the ads and resist buying the shortcuts, it’s free to play. However, it’s much more enjoyable if you spend the $2.99 to eliminate ads. And while an opponent technically could purchase his way to victory, I managed to win a good portion of matches
without buying anything. Thankfully, I have frugal friends.
TidBITS Watchlist: Notable Software Updates for 12 January 2015
Little Snitch 3.5.1 — Objective Development has released Little Snitch 3.5.1 with cosmetic refinements to the configuration user interface to better match the look of OS X 10.10 Yosemite. The network monitoring utility also fixes a rare issue that caused the app to hang when attempting to restart a computer after a first-time installation, fixes a bug introduced in version 3.5 that caused Until Quit rules to remain enabled after the process quit, improves compatibility with Xcode Server, and fixes an issue in the Network Monitor that caused the destination to display incorrectly as “0 Servers.” ($34.95 new,
free update, 21.2 MB, release notes, 10.8+)
Read/post comments about Little Snitch 3.5.1.
ChronoAgent 1.5 — Econ Technologies has released ChronoAgent 1.5, the synchronization and backup utility that works with Econ’s ChronoSync app to provide direct connectivity to a remote Mac. The update adds the capability to back up or sync over the Internet using the new WAN Access panel, and ChronoAgent can automatically configure the port-mapping functionality of your router. ChronoAgent 1.5 includes a built-in Dynamic DNS client that can connect to several popular services. Additionally, icons and supplemental artwork have been optimized for Retina displays, Notification Center support has
been added, and you can limit ChronoAgent’s access to files by approving only specific volumes. Version 1.5 also features a redesigned user interface and now requires a 64-bit Intel processor and OS X 10.8 Mountain Lion or later. Econ Technologies promises to update ChronoSync to version 4.6 in the coming weeks. ($15 new, free update, 9.0 MB, release notes, 10.8+)
Read/post comments about ChronoAgent 1.5.
ExtraBITS for 12 January 2015
In this week’s heaping helping of ExtraBITS: bank holding company Capital One has bought the Level One budgeting app, we take a look at how gadgets are having to adapt to the existence of smartphones, and manufacturers show off the (sorry) state of Apple’s HomeKit home automation framework. Plus, Philip Michaels pokes fun at CES at Six Colors, blogger David Sparks explains why he’s quitting Family Sharing, and Peter Cohen of iMore explains how to try out Windows 10 for free.
Level Money Purchased by Capital One — Bank holding company Capital One has acquired the Level Money budgeting app (see “Level Money Simplifies Budgeting,” 18 October 2013). The existing team will remain with Level Money, which will still be a standalone app. Terms of the deal were not disclosed, but Level Money stated that it has 700,000 users and has helped manage over $12 billion in transactions.
Gadgets in the Age of Smartphones — Smartphones have obsoleted an entire galaxy of gadgets, including cameras, music players, and handheld game consoles. What are gadget makers to do? As Farhad Manjoo explains in the New York Times, the answer lies in software. Specifically, gadgets that rely on software to create flexible platforms that can grow with their users and integrate with smartphones. But it’s worth keeping in mind that this approach doesn’t guarantee open connected systems; proprietary walled gardens are all the rage among
today’s tech giants.
The State of HomeKit — One of iOS 8’s touted features is HomeKit, which promises to unify home automation devices and allow them to be controlled by Siri. However, it wasn’t until this year’s Consumer Electronics Show that we got a glimpse of what manufacturers are working on, and so far it’s not pretty. The Verge reports that a number of devices they saw at CES were unstable, and that representatives said that Apple still has a lot of work to do. One fascinating tidbit: the Apple TV will serve as a bridge for HomeKit, enabling you to control
your home with Siri while on the road.
All You Need to Know about CES 2015 — Philip Michaels, writing for Six Colors, has penned a hilarious guide to CES 2015, summarizing everything you need to look out for. According to Michaels, we can expect Sony to publicly apologize to North Korea, Tim Cook to hold an incognito press conference outside a strip club, and actor Michael Chiklis (the Thing in recent Fantastic Four movies) to make awkward Internet of Things jokes. Of course, there will also be the usual assortment of lust-inducing products that will never see the light of day.
Why David Sparks Is Quitting Family Sharing — Attorney, author, and podcaster David Sparks has given up on Apple’s new Family Sharing feature. Sparks outlines several reasons for the decision, including the fact that in-app purchases and iTunes Match are not included in Family Sharing, some apps refused to update, and his family experienced disappearing playlists while Family Sharing was enabled.
How to Test Windows 10 on Your Mac for Free — If you’re curious about Microsoft’s upcoming Windows 10, Peter Cohen of iMore details how to install the Windows 10 Technical Preview on your Mac for free using the VirtualBox virtualization software. Cohen doesn’t recommend installing Windows 10 under Boot Camp yet, since it’s not officially supported.