TidBITS#1263/16-Mar-2015
We kick off this week’s TidBITS with a look at Meerkat, the Twitter-powered video-streaming app that could democratize live broadcasting — if Twitter doesn’t kill it first. Michael Cohen takes a look at Apple’s open-source ResearchKit and finds out what doctors have to say about it. Michael also contributes an overview of Fountain, a markup language that makes it easy to write a properly formatted screenplay. In a pair of editorials, Adam Engst posits that how you see the Apple Watch says more about you than it, and Rich Mogull explains why it’s a good thing that the CIA is trying to hack Apple products. Finally, we have the latest chapticle of Joe Kissell’s “Take Control of Security for Mac Users,” in which he explains how to surf the Web safely. Notable software releases this week include Security Update 2015-002 (Mountain Lion, Mavericks, and Yosemite), DEVONthink/DEVONnote 2.8.4, iMovie 10.0.7, Evernote 6.0.7, GraphicConverter 9.6, and Mailplane 3.4.1.
Chapter 8 of “Take Control of Security for Mac Users” Available
Perhaps your Mac’s most obvious connection to the outside world is via the Web, via a Web browser like Apple’s Safari or Google Chrome. There are numerous threats to your Mac’s security that come over the Web, and it’s important to learn how to protect yourself against them. That’s what Joe Kissell teaches you to do in Chapter 8, “Surf the Web Safely,” this week’s installment from “Take Control of Security for Mac Users.”
Joe starts off by explaining the utility of using encrypted connections when browsing, which is easy to do, and then walks you through the security-related settings in your Web browser. Then he discusses how to use passwords and credit cards safely on the Web, and how to avoid phishing attacks — unsurprisingly, relying on a password manager can be extremely helpful here. Finally, Joe closes the chapticle with a look at a couple of Web browser extensions that can enhance your security.
If you want to catch up with “Take Control of Security for Mac Users” so far, the first two chapticles are available to everyone, but all subsequent ones are limited to TidBITS members. Those who join the TidBITS membership program receive other benefits too (like 30 percent off all Take Control orders!), but what’s most important is that revenues contributed by TidBITS members have kept TidBITS running the last few years — your support has been essential. If you’re already a TidBITS member, log in to the TidBITS site using the email address from which you joined to read and comment on these chapters.
- Chapter 1: “Introducing Mac Security”
- Chapter 2: “Learn Security Basics”
-
Chapter 3: “Perform Quick Security Fixes”
-
Chapter 4: “Beef Up Your Security Settings”
-
Chapter 5: “Improve Your Passwords”
-
Chapter 6: “Improve Your Network Security”
-
Chapter 7: “Fortify Your Mac’s Defenses”
-
Chapter 8: “Surf the Web Safely”
We have four more chapters to go, and once those are in the can, the full ebook of “Take Control of Security for Mac Users” will be available for purchase by everyone in PDF, EPUB, and Mobipocket (Kindle) formats.
Meerkat Broadcasts Your Video to Twitter
Broadcasting live video on the Internet isn’t new. Neither is tweeting a link to a live streaming video. But put those two together in a simple package, and you have something that might just be revolutionary. That’s Meerkat, described by its founder as a “live video button for Twitter.”
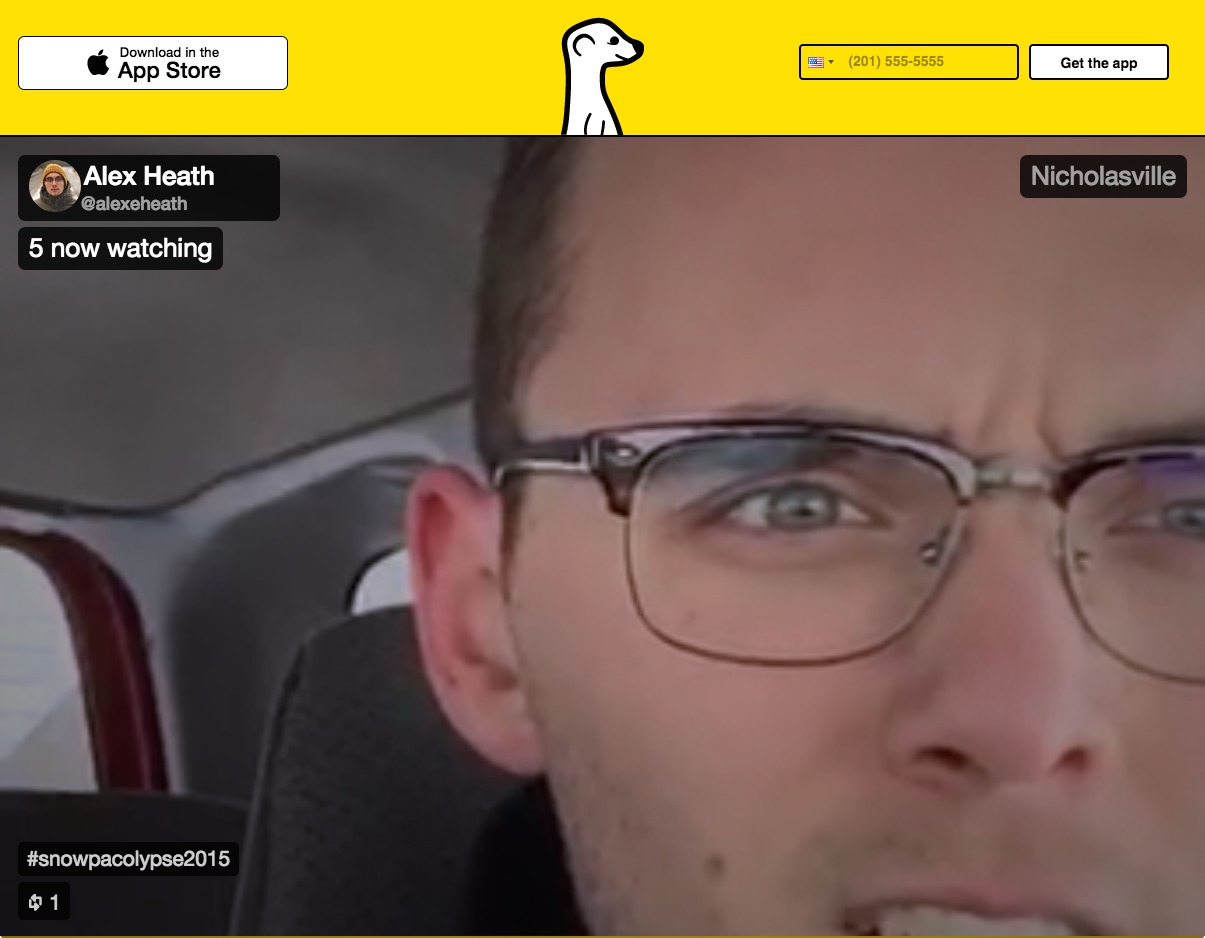
Personal Broadcasting — The free Meerkat app for iOS 8 makes it easy to stream live video from your iPhone or iPad to your Twitter followers. Just install the app, link it to your Twitter account, and tap Stream. Video from your device’s camera is instantly broadcast to the Internet, and Meerkat sends a tweet from your account with a link to the stream.
If you enter a description of the video before streaming, that will be included in the tweet. For instance, I ran a Meerkat stream called “Taking Your Questions,” where I answered random questions from people on Twitter.
Since your Twitter followers have to join the stream while it’s live, you can schedule a Meerkat stream instead of starting one without warning. When you schedule a stream, Meerkat posts a tweet with the time the stream is supposed to begin. When the time arrives, you receive a notification on your device. As soon as you open the notification, the stream begins and a tweet is posted with a link to the video.
While broadcasting, you see what’s being displayed to your viewers, along with their comments, overlaid with a button to reply to them on Twitter, plus buttons to activate the flash, switch between the rear- and front-facing cameras, and stop the video. Not surprisingly, typing to reply doesn’t work so well unless the iOS device is in a fixed position and you’re using an external keyboard.
As soon as you tap the Stream button, you’re live on the air, streaming from the device’s rear-facing camera. It’s unfortunate that there’s no option to set things up before the stream starts. Since I often want to address my viewers face-to-virtual-face (and spare them my messy desk), I cover the rear-facing camera with my hand when I start the stream, and switch cameras quickly after it starts.
Before you ask, no, your videos are not automatically saved to some cloud service, although you can save a copy of the finished video to your device. That’s freeing, since it gives you some leeway to express yourself without worrying about a flub going viral. (Of course, as with people taking screenshots of Snapchat, there’s nothing stopping someone from recording you with QuickTime Player.)
500 Million Channels and Nothing On — How would you find Meerkat video to watch, if none of your Twitter friends use it yet? To get started, search Twitter for “#meerkat LIVE” and browse around a bit. To avoid relying on searches or serendipity to know when others are broadcasting, you can follow other Meerkat users, and the app notifies you when one of them begins streaming. Streams can be viewed either in a Web browser or in the app itself.
Until recently, Meerkat would also notify you if someone you follow on Twitter began broadcasting. But Twitter has taken away Meerkat’s access to Twitter’s social graph, just after Twitter announced that it has purchased competing service Periscope. This is incredibly poor behavior on Twitter’s part, especially since apps like Meerkat are exactly what Twitter encouraged developers to create, after the company crippled third-party clients. The message Twitter is sending is: if you develop
something cool with our platform, we will steal it and then cut your product off at the knees.
Viewing Meerkat streams has some rough edges. If you view a stream by clicking a link on Twitter, it works reliably in your Web browser, though you must first log in to Twitter. However, viewing from the app itself is hit or miss. Opening a notification often takes me to the Web stream, instead of the Meerkat app.
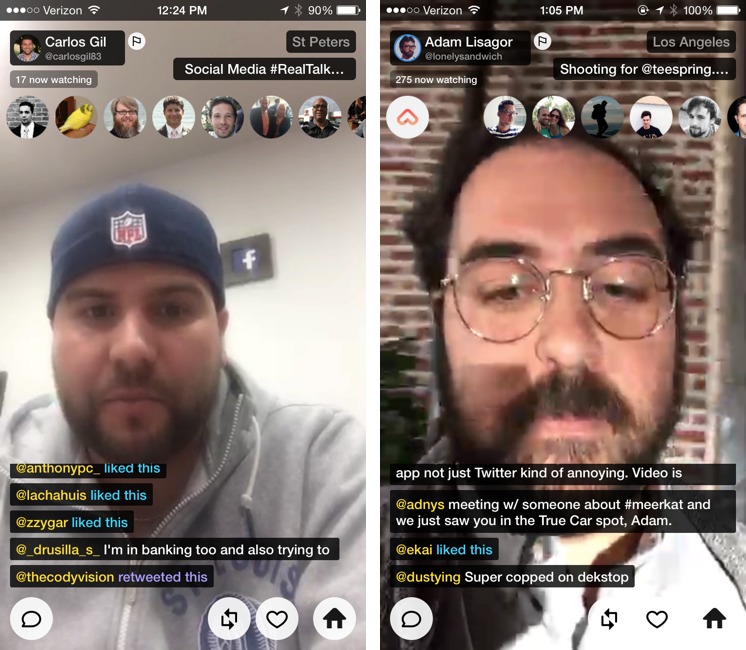
While you’re watching a stream in the app, Meerkat shows you the video, overlaid with bubble portraits of who’s viewing the same stream, as well as Twitter comments from viewers. There are also buttons to comment on the video (which uses Twitter’s @replies), retweet the video, favorite the video, and return to the home screen.
Pondering the Possibilities — Meerkat is such a simple idea, but it is exploding in popularity, at least if the constant notifications I receive about people I follow on Twitter joining are any indication. It has the potential to revolutionize journalism and broadcasting. You could use it to cover a protest, broadcast a city council meeting, or even stream an event for family members, like a graduation. For more active video, you might want something like a Hitcase or Velocity Clip. Of course, it could be used for uh… adult entertainment, and nothing in the rules precludes this.
Thankfully, and almost surprisingly, I haven’t stumbled across anything yet that required eye bleach.
What makes Meerkat so appealing is that it’s not just a platform for streaming video, but also for promoting it. But that has the potential to backfire, especially in these early days when many users are just giving it a spin. Many Meerkat users will launch a stream for only a few seconds, so that by the time you click on it, it’s already over. Promote something worthless and no one will give you a second chance.
If Meerkat is to last, and not become a flash in the pan like social media service Ello, the community needs to develop some conventions and etiquette around streaming so viewers know what they’re going to see, when they’re going to see it, and how long it will last.
If you do want to dip your toe into Meerkat, here are a few suggestions for broadcasting successfully:
- Schedule all videos, with a brief description of the planned topic and estimated length.
-
Have a plan for what you intend to do. Don’t just fire up a stream so we can stare at your nose hair for 30 seconds. Be interesting.
-
Announce on Twitter when the video has ended.
-
Delete the dead Meerkat links from your Twitter timeline after the video has ended.
Meerkat could make some changes that would help with these points. There needs to be a test or “setup” mode so broadcasters can prepare before going live. Also, Meerkat should have an option to tweet when the stream is finished and delete the original announcement tweet.
Regardless, Meerkat has a lot of potential, and if the community ends up using it in useful and interesting ways, it could become a significant force in democratizing broadcast video.
The Promise (and Limitations) of Apple’s ResearchKit
Fifteen minutes into the glittering product parade presented during Apple’s “Spring Forward” event on 8 March 2015, the presentation focused on ResearchKit, a non-glittery, pro bono initiative that seemed strangely out of place yet provided a real, and exciting, example of what mobile smart technology can do beyond allowing you to collect green chiclets in the Candy Kingdom.
Until now, much more has been heard from Google and Microsoft than from Apple in supporting academic research, so it’s nice to see Apple stepping up to the plate to help make the world a better place in ways other than just producing compelling products.
The Promise — As Apple glowingly describes it, ResearchKit is “an open source software framework that makes it easy for researchers and developers to create apps that could revolutionize medical studies, potentially transforming medicine forever.” Yes, the language is somewhat overblown, but, in fact, may turn out to be literally true.
Consider: today’s iPhone, which, in addition to lots of computing power, communication capabilities, and data storage, contains sophisticated sensors like an accelerometer and a gyroscope, along with a special processor to monitor and manage the data they provide.
Also consider: iOS includes HealthKit, which enables iPhone users to record physical activity through both automatic monitoring of the device’s built-in sensors and user input, and does so behind a sophisticated security system that protects the user’s privacy (see Rich Mogull’s Macworld article, “Why Apple really cares about your privacy”).
Next consider that much medical research involves studies that use human participants and that track certain facets of participants’ physical condition and behavior over time. In most cases, the more participants, the more useful and reliable the research findings — but also, the more expensive and difficult the research is to conduct.
Finally, consider that hundreds of millions of people already own devices that contain sophisticated sensing, security, and communication capabilities, devices that could be used to collect data from study participants, and at a scale and level of detail that heretofore has been, if not impossible, certainly expensive to deploy and difficult to manage.
If researchers could easily and reliably plug into the rich motion-sensing and health-related resources the iPhone offers in a way that protects participants’ privacy (de rigueur in any medical study), it could revolutionize medical studies and transform medicine.
That’s what ResearchKit promises.
In the long run.
What We Have Now — For the moment, though, ResearchKit exists as a relatively small software framework for building iOS apps that collect and manage medical research data, along with a few apps that researchers have developed with the framework.
The apps serve as demonstrations of what ResearchKit can do, and you can download them yourself if you like. But they also are actual research tools, and have already begun to yield substantial benefits to researchers: within 24 hours of the Apple event, 11,000 people signed up for one study, something that would normally take a year and cooperation among 50 medical centers.
The ResearchKit framework itself, due to be released as open source in April 2015, is relatively small and unambitious. Currently, it consists of three modules:
- Surveys: Many studies involve surveys to which participants respond. ResearchKit provides a localized user interface with which researchers can specify their questions.
- Informed Consent: All medical studies require the informed consent of participants whenever personal health information is collected; ResearchKit offers a number of templates that researchers can customize to provide the information required in order to request such consent, as well as methods for acquiring consenting participants’ signatures. Researchers can also create comprehension tests with this module that help make sure participants understand just what they are consenting to.
-
Active Tasks: This module currently provides five subsidiary modules that researchers can use to collect data from the iPhone’s sensors. These include Motor Activities, such as gait and coordination, making use of the accelerometer, gyroscope, and touchscreen; Fitness, which uses the accelerometer; Cognition, which employs the touchscreen; and Voice, which uses the microphone. Support for data returned by the sensors in the Apple Watch (which can, among other things, detect heart rate) is also provided by some of the Active Tasks modules.
However, ResearchKit itself does not provide for secure communications between the deployed app and the researchers’ server, it doesn’t give access to passively acquired background data, nor does it provide the capability to schedule tasks or surveys; iOS has other programming frameworks that can handle those needs.
Also lacking is any automatic compliance with federal or international research regulations and guidelines: researchers are responsible for implementing such compliance.
What Doctors Think — Many of those in medicine are thrilled by the possibilities that ResearchKit offers. For example, Dr. Norman Cohen, a professor at Oregon Health Sciences University, told me, “ResearchKit has the potential to be a real game-changer. As an anesthesiologist, I am always looking for ways to help patients have improved surgical outcomes. ResearchKit could provide a method to measure the impact of interventions, such as diet modification, physical pre-conditioning, glucose control, and medication management on outcomes across large numbers of surgical patients. The
framework may also be able to improve patient education, engagement, and compliance with care pathways. These are exciting possibilities as we institute Perioperative Surgical Homes in an effort to improve the value of care we deliver.”
Others are less sanguine. Dr. Phil Jones, Associate Professor at the University of Western Ontario, has his doubts, saying, “You cannot simply ‘crowdsource’ medical research. There must be some minimal checks and balances, and those checks and balances are precisely what ResearchKit is currently missing.” He provides several examples of where today’s ResearchKit falls short, including design holes that could allow selection bias, attrition bias, and observer bias to corrupt a study’s findings.
Nonetheless, even Dr. Jones isn’t a complete naysayer, concluding his analysis of ResearchKit’s flaws on an upbeat note: “However, the future is bright! I have no doubt significant improvements will be made that will enable high quality, high fidelity research to be done using smartphones and ResearchKit.”
If researchers, and Apple, actively devote the time, resources, and ingenuity needed for ResearchKit to fulfill its promise, the future may indeed be bright: the results of that study are yet to be compiled.
Formatting Screenplays with Fountain
I’ve lived most of my life in the Los Angeles area, and although L.A. is a sprawling diverse megalopolis, it’s also an insular industry town, with the industry in question being what we Angelenos refer to as “The Industry”: that is, show biz (it’s like no business — I know!). In fact, I am so much an Angeleno that the undergraduate degree I received from UCLA in the mid-1970s was for Motion Picture/Television Production, with an emphasis on screenwriting.
The screenplay format in use back in my student days had remained unchanged since the advent of talking pictures: scene openings had a distinct typographic look, as did action descriptions, scene transitions, and dialog. This format required a deft hand with a typewriter’s tab function, since almost every screenplay element had its own indentation.
Amazingly, despite all the changes in today’s digitally mediated twenty-first century, the screenplay format remains the same, down to the requirement that the text be in a standard monospaced typewriter font — not, in fact, merely an arbitrary nod to tradition but a practical requirement. As it turns out, a typical screenplay page, properly formatted, often (though certainly not always) works out to about one minute
of screen time. And, in the movie business, running time is money!
More importantly, though, screenplay format is designed for easy reading, annotation, and skimming rather than for the economical use of paper or ease of data entry. It features plenty of space for handwritten notes, and it makes all of a script’s elements visible at a glance. However, unfriendly as the format was to typewriters back in my youth, it is just as unfriendly to word processors today.
Luckily, even though most general-purpose word processors are not designed to support screenplay format effortlessly, computers still make the task of writing a screenplay much easier. Here’s the trick: you don’t need to write in the rigid screenplay format to produce a properly formatted screenplay! Instead, you can defer the formatting until later: back in the day, for example, I used to draft my scenes on a yellow pad by hand and only type them up, in proper format, when they were done. Today, I can compose them in any text editor without worrying about format and have them laid out in proper format later. All I need to do is obey a few simple rules as I write. And what is the source of these rules? A markup system known
as Fountain.
Similar to, and inspired by, the Markdown syntax developed by John Gruber (itself inspired by Ian Feldman’s setext format created with Adam Engst for TidBITS back in 1992), Fountain text can be written with any text editor and then run through a simple converter to produce a formatted screenplay. And, even more so than Markdown, the Fountain syntax is easy to remember and uncluttered, so the text is easy to read and to understand even before it is converted to standard screenplay format.
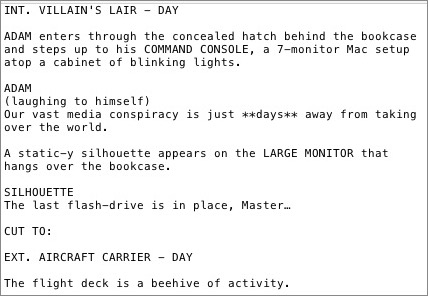
For example, in a screenplay, scene headings nearly always consist of a single line, in all caps, indicating whether it is an interior or exterior scene (important when budgeting a production) and whether it is day or night (a detail your cinematographer and key grip really want to know). Dialog begins with a character’s name, again in all caps, centered on a line by itself, followed by the speech itself, in a narrow column below the name (possibly prefaced by a parenthetical performance instruction) — easy for an actor to find when skimming the script, and easy for an actor to read when running lines. Transitions, like scene headings, are also in all caps, but they are usually right-aligned, again to make them easy to spot.
As it so happens, the rigid format turns out to be a boon to the Fountain markup syntax. Take scene headings: they nearly always begin with a key abbreviation, usually INT or EXT, so any line in all caps beginning with one of those abbreviations is easily identifiable as a scene heading. Similarly, dialog is always headed by a character’s name, again in all caps, so any line consisting only of an all-caps word or two (that isn’t INT or EXT) can be identified as the beginning of a dialog
section. Transitions are also in all caps, and they end with “TO:”, so any line of all-caps text ending in “TO:” is considered a transition instruction. And other text? By and large, that is treated as an action description.
As a result, the Fountain version of a scene usually has almost no special extra formatting markup to distract the writer (and, trust me, writers yearn for distractions) — the Fountain text already looks much like a screenplay, just one that is left-justified throughout.
The Fountain syntax, of course, has additional features for adding notes, overriding default formatting (so you can have a character named INT if your screenplay about C compilers requires it), marking deleted passages, and so on. But nearly all of those features are exceptions. Generally, you can learn the Fountain syntax rules you need most often in a matter of minutes, and then you can write your masterpiece with any text editor or word processor
you have handy, whether on a Mac, an iPad, an iPhone, or any other digital device that lets you compose plain text documents.
But what about converting the plain text Fountain documents you create into a properly formatted screenplay? Fortunately, that is not much of a problem either: there is a bevy of apps (including such writer-oriented apps as Literature & Latte’s Scrivener) that can handle Fountain markup, and you can even find Web apps, such as AfterWriting, that can convert Fountain text into screenplay format. There are also apps designed specifically to use the Fountain format, such as Quote-Unquote Apps’ Highland and its companion iOS app for viewing Fountain
files, WeekEnd Read. (I’ll take a closer look at these two in a forthcoming TidBITS article.)
Of course, professional screenwriters with a movie or two under their belts can afford several hundred dollars for high-powered apps like the industry-standard Final Draft to compose their next Oscar-contending script. But for the waiter/barista/screenwriter-about-town hoping to break in to The Industry, Fountain provides an easy low-cost entry to the craft.
(By the way: why the name “Fountain”? It’s a reference to Fountain Avenue, a stretch of road that runs right through the heart of Hollywood.)
Apple Watch: Your Personal Technology Rorschach Test
With Apple’s announcement of pricing details and a ship date (24 April 2015) for the Apple Watch, the technology echo chamber has gone into overdrive, with predictions ranging from complete flop to mind-blowing success. The truth undoubtedly lies somewhere in the middle, since failure is almost inconceivable for a product with Apple’s design and engineering chops behind it, not to mention the company’s marketing muscle and unlimited budget. On the flip side, the Apple Watch cannot possibly match the iPhone in terms of success, not least because it requires an iPhone and offers little functionality that goes beyond what the iPhone provides.
Here’s where the Rorschach ink blot test starts — what you think about the likely success of the Apple Watch probably says quite a bit about how you view Apple. Those of us who pay close attention to Apple seldom bet against the company, since Apple has repeatedly proven its ability to identify a target market, meet that market’s needs, and continue to execute over time. But we’re also victims of selection bias, since there are an awful lot of people out there who know or care little about Apple, many of whom may have iPhones, but a majority of whom rely instead on Android smartphones.
Here’s an experiment to try. Identify several friends who aren’t involved in the tech industry in any way, explain the Apple Watch to them, and see if they think they’d be interested. I did this with a friend who’s a massage therapist and does all her work on an Android smartphone and tablet, both purchased because they were cheaper than the iPhone and iPad. She had no trouble understanding what the Apple Watch offered and even picked up on the fashion angle for some potential buyers, but was shocked at the pricing and was concerned about what would happen to it in several years.
It’s particularly interesting to see how people react to the Apple Watch’s pricing. Previously, Apple had said only that the Apple Watch would start at $349, generating vast amounts of speculation about how the more expensive models would be priced. It was all wasted brain cycles, of course, because it’s not as though you could change your behavior in any useful way based on a prediction, correct or not. Now we know that the Apple Watch Sport will cost $349 (38 mm) or $399 (42 mm), the Apple Watch will range from $549 to $1,099 depending on size and band, and the gold Apple Watch Edition will start at $10,000 and top out at $17,000.
How you view those prices is another ink blot in the Rorschach test. Personally speaking, I grew up on a small farm and for the first 10 years of my life, my parents were trying to be entirely self-sufficient. Even after they eventually settled for jobs, their income didn’t hit some definition of middle class until I was almost out of high school. In short, it’s hard for me to spend money at all, and that’s exponentially true for luxury items.
Yes, I’ll buy an Apple Watch Sport because it’s essential for our business that I know about it (and as an athlete, I want to evaluate Apple’s fitness claims), but I’d have a hard time justifying the mid-level Apple Watch, and the Apple Watch Edition is utterly unimaginable for me. If I’m going to buy something, it needs to be highly functional and improve my life in a real way. But that’s me, and clearly, lots of people spend vast sums of money on luxury items that have no practical value — they’re shopping for entirely different reasons.
Where I suspect many long time Apple customers feel discomfort is not actually in the prices, but the fact that Apple is presenting us with a purchasing decision that doesn’t hinge on quantitative specifications, and instead on intangible factors like emotion, desire, and affirmation of social status. That’s a major shift. Apple has never before presented us with a model choice that couldn’t be resolved by evaluating functionality. Spend more on a desktop Mac and you get more performance or a larger screen. Spend more on an iPhone or iPad and you get more storage or better connectivity. Increased price has always been associated with a quantitative benefit, and you can match that to your functional needs. For those of us who
instinctively avoid luxury brands, being given a choice between different Apple Watch models that are functionally identical is uncomfortable.
Plus, while Apple has changed over the years, this is the company whose first Macintosh marketing slogan was “The computer for the rest of us.” While never the cheapest, Apple’s technology has always been welcoming and inclusive, and the Macintosh was a force for the democratization of technology, breaking down hierarchies and control structures. The iPod and then the iPhone may have had an elitist cachet briefly, but quickly became so widespread that using one in public in no way made a statement about class or wealth.
With the Apple Watch, though, Apple has changed the equation. Paying more doesn’t get you a more functional Apple Watch, it gets you a more expensive Apple Watch that everyone can see on your wrist. Does the stainless steel Apple Watch really cost $200 more to make than the aluminum Apple Watch Sport? Is there really $10,000 worth of gold in the Apple Watch Edition? Of course not. Apple is setting these prices so consumers can choose how much they wish to spend and in doing so, make a statement about what sort of people they are and what socio-economic class they belong to. I wonder if I’ll ever see an Apple Watch Edition in the wild.
Regardless, the next Rorschach ink blot comes when pondering the future of the Apple Watch. The only statement from Apple on this topic is that the battery is replaceable; TechCrunch claims the battery will last around three years. The bigger question is if Apple will make upgrades to the Apple Watch available.
Those who are dubious of Apple’s commitment to current customers (as opposed to attracting new ones or generating upgrade revenue) will consider the Apple Watch a dead-end purchase that will end up in a drawer alongside that old iPod nano. It’s not like you can upgrade any other Apple device these days. Conversely, optimists who like to imagine the most efficient technological solutions will instead posit that Apple will come up with a way of swapping the guts of the Apple Watch for newer hardware. That would also protect the future value of the Apple Watch Edition for those who can’t imagine buying a $10,000 watch that may lose its functionality in a few years.
Extend that to the next generation of the Apple Watch. I think there will be one. As Jeff Carlson, author of our “Apple Watch: A Take Control Crash Course,” commented in a staff discussion, the investment in research and manufacturing infrastructure to make the Apple Watch is staggering. Even if this initial model of the Apple Watch isn’t an instant best-seller, Apple will continue to add capabilities (standalone GPS and a waterproof case, please!) and further miniaturize the components. Or at least that’s how I see things, since I’m a technology optimist — I always see better gear just around the corner. But that’s a long way to look into the future — not
everything Apple touches turns to gold, and I suspect that those who believe Apple hasn’t been the same since Steve Jobs died may see the Apple Watch as indication of how Apple is continuing to wander.
Personally, once I tamp down my discomfort with how Apple has positioned and priced the different Apple Watch models, I’m excited to get my hands on one and see how it integrates into my life. And once I do, I’ll hold out hope that becoming addicted to the Apple Watch won’t result in a $400 biennial tax and a trail of obsolete hardware, either because the initial model holds its own functionally for much longer or because Apple provides some sort of hardware upgrade to keep it sufficiently capable. But that’s just me. How about you?
The Good News about the CIA Targeting Apple
On 10 March 2015, The Intercept revealed how the U.S. Central Intelligence Agency targets Apple hardware and software. Based on top-secret documents exposed by Edward Snowden, the article implies that Apple’s Xcode development environment, iOS encryption keys, and Software Update may all have been compromised by the CIA in the name of broad surveillance. Fortunately, the truth is more nuanced.
While I have no doubt the CIA (and every other intelligence agency and criminal organization in the world) targets Apple along with all the other major technology companies, that doesn’t mean they necessarily succeed, or that any successes last long. It’s also important to note that most of the attacks listed in the article are better suited for targeting individuals, not the mass spying that has so dominated the headlines.
Apple has been a particular target since the company started taking privacy and security both seriously and personally — even beginning to architect parts of its products and services to resist government-level attacks. But Apple isn’t perfect. The company still struggles to find the right balance between security, privacy, design, and usability in the face of advanced criminal- and government-level attacks.
The Intercept’s piece was mostly a condemnation of government tactics, but failed to address what matters to Apple’s customers — whether Apple’s products remain secure and safe to use. Overall, the information is quite optimistic, but the article highlights the complexities of modern security, privacy, and intelligence gathering. We are still in the early days of what is likely to be a generational issue as society continues to adjust to the digital age.
Because That’s Where the Intelligence Is — As a taxpayer, if the CIA and every other U.S. intelligence agency doesn’t target Apple products, I want a refund.
Our instinct is to express outrage at U.S. intelligence agencies targeting the products of U.S. companies, but this is far from the first time it has happened, is far from the last time it will happen, and is absolutely essential for those agencies to do their jobs. As the entire world relies completely on technology for all forms of communication, tapping into that technology is critical for intelligence gathering.
As much as it might pain me to live in a world that requires spies, that’s the reality. When U.S. companies dominate a tech sector, it’s only natural that intelligence agencies will target their products. We in the security industry have long suspected that agencies have planted employees in manufacturers and supply chains or engaged in direct operations, in most cases targeting products destined to specific countries. Over the past two years, those rumors and jokes at the bar at security conferences have migrated to the headlines.
While The Intercept’s article focuses on Apple, it also mentions intelligence agency attempts to target Microsoft and the chip manufacturers who make the Trusted Platform Module (not a Microsoft-specific product) used to help power encryption in various platforms. This is on top of previous leaks indicating potential government attacks that have compromised all sorts of encryption hardware, software, and services.
Put bluntly, intelligence agencies must target U.S. companies since those companies’ products — whether we’re talking the iPhone or Windows — are used by all their international targets.
I actually find The Intercept’s article highly encouraging. The fact that government researchers needed to expend such intense effort to access devices and services shows that the security technologies Apple and others provide for us are effective (if not perfect) and the technology companies aren’t simply rolling over for the intelligence community, which would be far more concerning.
Hard Targets — Much has happened in the security world since 2012, when the documents revealed by Edward Snowden were created, including major changes to the iOS security model. Let’s look at the main products mentioned in the documents, and what the risks are.
Keep in mind, I’m not dismissing these risks. But by every reading they seem targeted, temporary, and self-limiting.
Xcode is the tool all Mac and iOS developers use to create applications. The government researchers claimed that they created a cracked version of Xcode that could embed attack code into any apps created using that version, without the developer knowing about it. If someone were able to compromise the canonical version of Xcode distributed by Apple, it could affect every application, anywhere. It’s the sort of thing that keeps security-conscious developers up at night.
Compromising a developer tool chain, especially a compiler, is as bad as it gets. Imagine the capability to insert malicious code into major, popular applications without the developer knowing about it. But believe it or not, there is an upside here. Based on the researchers’ presentations, they don’t have access to the canonical version of Xcode itself, but instead need to target a particular developer and swap out his copy of Xcode on his particular computer. That’s the sort of attack I’d rather see, since it means intelligence agencies can target developers in foreign countries on an individual basis (to get to the users of a particular developer’s apps), and not compromise the entire ecosystem of Apple
development.
Even if the CIA were able to get to the canonical version of Xcode, every Xcode update could eliminate the malicious version, unless the Software Update mechanism were also compromised, depending on how often the developer updates.
In fact, software update mechanisms are another high-value target, and one the documents indicate government researchers have worked on. But as with Xcode, unless Apple’s entire Software Update infrastructure were compromised, the attack is limited to specific targets.
iOS encryption is so effective that law enforcement agencies want the government to compel Apple to provide a back door. It’s no wonder intelligence agencies want to crack it. According to The Intercept, researchers targeted the Group ID key used by all Apple devices sharing the same hardware. While this key could help an attacker install malicious software on the device, it can’t be used to recover data on the device if the user sets a good passcode.
There is some nuance here, in that a malicious system software update could potentially expose all the data on a device under some circumstances (the user doesn’t know it was installed, and keeps using the device). Cracking the GID key can’t, for example, allow law enforcement to extract data without the device being unlocked and accessed. If that were true, Apple (as holder of the GID key) could access any user’s data for any law enforcement agency, which the company has explicitly and vociferously claimed is impossible.
In each case, the attacks are serious, but they also show just how hard it is to break into Apple devices, especially iOS devices. None of the attacks seem well suited for mass surveillance, since that would increase the potential for exposure. As the researchers themselves stated:
The Intelligence Community (IC) is highly dependent on a very small number of security flaws, many of which are public, which Apple eventually patches.
In short, the intelligence community wants to keep their attacks secret so they can be used in highly targeted ways, against specific people. I can live with that.
For Apple, It’s Personal — Since those 2012 presentations, Apple has taken even stronger stances to improve security and privacy. In a Macworld article last year, I mostly attributed this to economic reasons, but in ongoing background conversations with people at Apple, it has become clear they take privacy personally.
As an industry analyst, I tend to think of corporations as being driven purely by the bottom line, but that isn’t always the case. Even eliminating any altruistic motivations, Apple is a company where the employees’ entire lives revolve around both the creation and the use of their products and services.
I’m pretty sure the thought of being spied upon gives Apple executives and employees the same itchy feeling that the rest of us feel. Worse, I think they feel that they will have failed technically if their products turn out to be easily hacked — there’s little that developers hate more than being shown how their code could be subverted. No one wants to see the sort of condemnations Apple faced when a simple programming mistake led to a serious flaw in SSL.
This shows through in Apple’s product decisions. iCloud Keychain can be configured to be essentially NSA-proof (see “How to Protect Your iCloud Keychain from the NSA,” 1 March 2014). Apple even physically destroys the hardware smart cards needed to access key management appliances on the off chance that an employee is actually serving multiple masters.
Both FaceTime and Messages support end-to-end encryption. Apple can technically manipulate and change that process, but not easily since it would require what appears to be a major architectural update. And the company’s stance on iOS encryption is clear.
Think about it from Apple’s position. For reasons beyond its control, Apple is now the biggest technology target in the world, from criminal organizations, foreign intelligence agencies, and even its own government. And what is being targeted are the tools and services that all Apple employees rely on every moment of every day. It’s hard to find greater motivation to double down on security and privacy, and the fact that even CIA researchers struggle to maintain offensive capabilities against Apple products shows that these security investments pay off.
That’s strong motivation, especially since it’s the job of spies to spy, even when it means finding flaws in products made at home, used abroad. Apple security isn’t perfect — new flaws will continue to be revealed, likely more often than any of us would like — but now that Apple has upped its security game to block even the most capable intelligence agencies in the world, the main beneficiary is the average user.
TidBITS Watchlist: Notable Software Updates for 16 March 2015
Security Update 2015-002 (Mountain Lion, Mavericks, and Yosemite) — Apple has released Security Update 2015-002 for OS X 10.8 Mountain Lion, 10.9 Mavericks, and 10.10 Yosemite. Most noteworthy is the fix for the FREAK vulnerability (short for Factoring RSA Export Keys), which could enable an attacker to intercept SSL/TLS-encrypted traffic and then access or alter communications between the client and server. Security Update 2015-002 also addresses a vulnerability in IOAcceleratorFamily and IOSurface’s handling of serialized objects for all three operating systems. For Yosemite, the Security Update patches leaking
kernel addresses and heap permutation values from the mach_port_kobject kernel interface and improves bounds checking for iCloud Keychain to contain multiple buffer overflows. Security Update 2015-002 is available via Software Update or via direct download from Apple’s Support Downloads Web site. Note that there are two updates available for 10.10 Yosemite — one for Early 2015 Macs (i.e., those announced last week; see “New 12-inch MacBook Joins Updated MacBook Air and MacBook Pro,” 9 March 2015) and one for older Macs. (Free. For 10.8 Mountain Lion, 177.3 MB; for 10.9 Mavericks, 62.3
MB; for 10.10.2 Yosemite, 5.4 MB; and for Yosemite on Early 2015 Macs, 5 MB)
Read/post comments about Security Update 2015-002 (Mountain Lion, Mavericks, and Yosemite).
DEVONthink/DEVONnote 2.8.4 — DEVONtechnologies has updated all three editions of DEVONthink (Personal, Pro, and Pro Office) and DEVONnote to version 2.8.4. The three editions of DEVONthink and DEVONnote simplify how files and folders are moved into databases from the Finder by adding the capability to drag items while pressing the Command key. This action imports the files and sends the originals to the Trash. The four apps also add new date-related smart group conditions, improve compatibility with OS X 10.10.2 Yosemite (resolving
glitches in the group selector and the Groups & Tags panel, plus page up/down keyboard handling of PDF views), add support for .webhistory and .webbookmark bookmark files, retain tags of documents after splitting them, and improve the French localization. (All updates are free. DEVONthink Pro Office, $149.95 new, release notes; DEVONthink Professional, $79.95 new, release notes; DEVONthink Personal, $49.95 new, release notes; DEVONnote, $24.95 new, release notes; 25 percent discount for TidBITS members on all editions of DEVONthink and DEVONnote. 10.7.5+)
Read/post comments about DEVONthink/DEVONnote 2.8.4.
iMovie 10.0.7 — Apple has released iMovie 10.0.7 with support for browsing and adding content from Moments, Collections, Favorites, and Albums in the new Photos for OS X app (currently available only as a beta version; see Jason Snell’s “Initial Impressions of Photos for OS X Beta,” 9 February 2015). iMovie now always displays Play/Pause, Prev/Next and Full Screen buttons below the Viewer for easier navigation, and makes the Record Voiceover button available below the Viewer for easier access when adding narration. The update also adds support for the Sony XAVC-S format
and addresses unspecified stability and compatibility issues. ($14.99 new from the Mac App Store, free update, 2.0 GB, 10.10+)
Read/post comments about iMovie 10.0.7.
Evernote 6.0.7 — Evernote has released version 6.0.7 of its eponymous information management app to try to tame high CPU usage and improve general note editing sluggishness, though a larger fix is promised for the next version to resolve these issues fully. The update ensures that the Attachments button shows all shared notes and notebooks in a Work Chat, enables you to customize the toolbar to meet your needs, fixes an issue with dragging and dropping an image in a note (and now always appends attachments to the end of a note), fixes an issue with pasting URLs containing & or ? characters on OS X 10.9 Mavericks, and fixes a bug with searching PDFs. As of this writing, the Mac App Store edition was still stuck at version 6.0.6. (Free from Evernote or the Mac App Store, 64.6 MB, release notes, 10.7.5+)
Read/post comments about Evernote 6.0.7.
GraphicConverter 9.6 — Lemkesoft has released GraphicConverter 9.6 with a variety of new features and improvements for the venerable graphic conversion and editing utility. The update adds support for Photoshop Pattern file import, a batch SVG-to-PDF (vector) conversion, support for pressure-sensitive pens by the Brush tool, an automatic Red Eye feature, the capability to shift channels left and right, and support for importing and exporting BPG (Better Portable Graphics) image files. It also improves MIME decoding, shows a marker in the Open Street Map display, ensures that corrupt GPS data will no
longer report that a file has any GPS data, and updates the Norwegian localization. ($39.95 new from Lemkesoft or the Mac App Store, free update, 234 MB, release notes, 10.7+)
Read/post comments about GraphicConverter 9.6.
Mailplane 3.4.1 — Uncomplex has released Mailplane 3.4.1, which solves a longstanding crash associated with the Streak customer relationship management plug-in. The Gmail-specific email client also now enables you to set how Mailplane handles image conversion, adds support for using the two-finger slide gesture to go back or forward in the browsing history, enables you to define hotkeys for Compose Note to Self and Toggle Do Not Disturb (via Preferences > Shortcuts), and notifies you (with an “M” in the status bar) if there are errors or connection issues. ($24.95 new, free update, 34.3 MB, release notes, 10.7+)
Read/post comments about Mailplane 3.4.1.
ExtraBITS for 16 March 2015
In this week’s collection of links, Adam Engst discussed Apple’s latest announcements on The Tech Night Owl podcast, Google revealed a new Chromebook Pixel, we found out if Apple’s switch from MagSafe to USB-C will endanger the 12-inch MacBook, product designer Greg Koenig examined the Apple Watch’s manufacturing process, the Wall Street Journal explained how Apple is taking over your local mall, and Josh Centers spoke about the CIA hacking Apple on The Dan Benjamin Hour.
Adam Springs Forward on The Tech Night Owl — On the latest episode of The Tech Night Owl Live, Adam Engst joins host Gene Steinberg to talk about the many announcements at Apple’s “Spring Forward” event, including the Apple Watch, the 12-inch MacBook (with a focus on USB-C and the new keyboard), and the Apple TV’s price drop.
New Chromebook Pixel Challenges 13-inch MacBook Pro — It’s not aiming at Apple’s tiny new 12-inch MacBook, but Google’s new second-generation Chromebook Pixel boasts specs and prices that compete directly with the 13-inch MacBook Pro with Retina display (for context, see “Google’s Chromebook Makes for a Fine Auxiliary Laptop,” 24 February 2014). The new Chrome OS-based laptop is slightly smaller and lighter than the MacBook Pro yet features a 12.85-inch, 2560-by-1700 Retina-level touchscreen and can also drive an external 4K display. In terms of connectivity,
it has two USB-C ports for charging and peripherals, two standard USB ports, and an SD card reader, along with dual-band 802.11ac wireless and Bluetooth 4.0 (no LTE option this time, alas). Its battery lasts up to 12 hours, and it has a 720p video camera. There are two models, one with a 2.2 GHz Intel Core i5, 8 GB of RAM, and 32 GB of flash storage for $999, and another with a 2.4 GHz Intel Core i7, 16 GB of RAM, and 64 GB of storage for $1,299.
Will the New MacBook Crash to the Ground? — With the new MacBook abandoning MagSafe for the new USB-C standard for charging, many Mac owners are wondering if Apple’s newest notebook will be vulnerable to potentially disastrous cable snags. The answer is yes: the MacBook can be dragged off a desk by its charging cable. Over at Macworld, Glenn Fleishman provides proof in the form of some impressively detailed Newtonian physics.
Examining How the Apple Watch Is Made — If you’re intrigued by the design of the Apple Watch and wonder how it’s actually made, you’ll want to read this detailed blog post by product designer Greg Koenig. Koenig goes through the Apple Watch manufacturing videos step by step, describing the process and giving context on materials and techniques.
Apple Stores Drive Mall Traffic — Traditionally, so-called “anchor stores” have been the main attractions at shopping malls. But as old-fashioned department stores become less relevant, Apple is becoming a major driver of mall traffic. An Apple Store can lift mall sales by 10 percent, and as a result, Apple can get much better deals on rent than similarly sized stores.
Josh Centers Talks CIA Hacking on The Dan Benjamin Hour — Managing Editor Josh Centers called into The Dan Benjamin Hour to discuss revelations that the CIA is working to break the security of Apple devices. Josh gives an overview of what’s been revealed, and offers some insight into what average users can do to protect themselves (not much).